Ethical Hacking Fundamentals: Exploring Information Gathering Techniques
September 28th, 2023
By: Ryan Morrissey and Annabel Otutu
Information Gathering in Pentesting
Information Gathering is a set process for collecting data and conducting research that can be used to uncover information on a potential target. Getting to know the environment to be exploited is an important step in the hacking process. When a Red Hat pentester plans to attack a system, they must go through a whole process of passive scouting and research with the purpose of finding an area of interest to exploit that would give them access to the system. This is done by following a set scope that has been provided by a client. Hackers do this with the aim of finding and exploiting vulnerabilities.

A hacker scouts systems without drawing attention while they gather information. An application that scans the network for open ports can carry out system scanning. It then displays any that meet specifications. Possible exploitations can also be carried out by applications as well as possible vulnerabilities depending on what they find. Ports that are not in use can be closed to prevent ports from being exploited. Unwanted open ports can make your network unsafe. Configuring rules on your firewall can help make sure ports are protected. Port scanning of your own network and filtering port traffic. Blocking or allowing network packets into or out of your network based on their port number is another way of keeping your network safe. In this phase, the attacker gathers as much information as possible to be utilized when penetrating the target during the exploitation phase. The more information gathered during this phase, the more options there are for the attacker to choose from to use against the system.
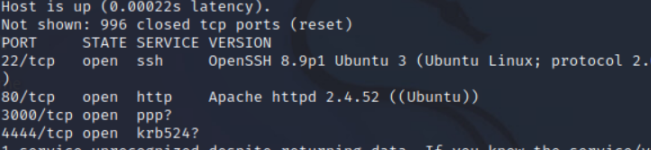
Understanding Weaknesses and How They Can Be Exploited
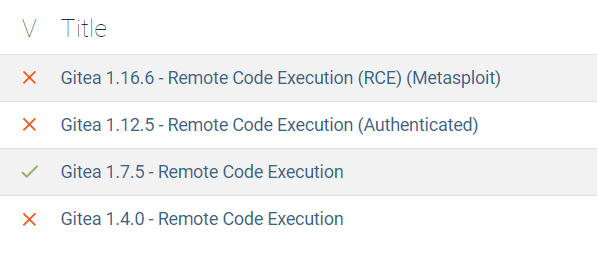
While planning an attack, if something stands out to an attacker, they take note of it as a potential exploit. Often at times, online forums and blogs document applications with known vulnerabilities. This information is easily accessible to hackers. In the case below, the targeted software (Gitea) a specific version with a known vulnerability, is being used on the target’s pc. Companies are always striving for their software to be safe and running at its best. When a major bug or exploit is found, a new version is made as soon as possible. Regular updates are made available to users. Updating to these newer versions can keep users safe from known vulnerabilities. While this doesn’t make the software bulletproof, it still blocks or slows down attackers from finding ways in.
Common Hacking Techniques
Hacking techniques are steps a hacker takes that go into exploiting vulnerabilities in order to gain unauthorized access to any computer, phone, or network system. Hacking techniques are ever-evolving with the times, and it’s important to keep up with new threats so there is hope of defending people and systems against them.
1. Phishing
While phishing attacks are a very common method of attack, others create a way to force themselves in. But how does one defend such a method and why does this work?
Phishing attacks depend on tactics used to trick individuals into revealing sensitive information like login credentials and credit card numbers. While phishing is a common method of attack, there are other techniques cyber criminals make use of to infiltrate systems. To defend themselves against these various methods effectively, individuals and organizations must have a fully implemented security program. One important aspect of defense is education and awareness. Users in an organization should be trained to recognize phishing attempts and other suspicious activities. Regularly updated cybersecurity training programs can help individuals stay informed about the latest tactics that are being used by cybercriminals. By staying vigilant, keeping software up to date, and adopting security best practices, individuals and organizations can significantly reduce their vulnerability to a wide range of cyber threats.
2. Bruteforce/Guessing
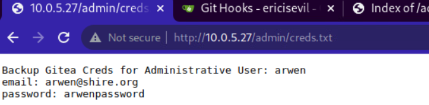
Thanks to the scouting process, not only did the user find a way to exploit the version of Gitea, but they also gained an important piece of information in the scouting process. While they were investigating the user’s IP, they found a webpage was open and contained something crucial; the user’s username and password into gitea. With this, the attacker has been given the keys to the system. Once the user completed their exploit, they got into the user’s login which, thanks to guessing and brute force, found out the password for the user was the exact same. It’s important to keep passwords in a secure place and to also keep a unique password for all different logins. Keeping passwords kept on a webpage can lead to scenarios such as this; it’s better to keep passwords on something physical and written down in a secure location.
3. Viruses
Individuals and organizations need to guard themselves against viruses. What are viruses? Viruses are malicious software programs that can replicate themselves and spread to other files and systems much like biological viruses. They attach themselves to legitimate programs or documents, which makes them appear harmless until they are opened. When the virus gets activated, it can perform a variety of harmful actions, from corrupting data to stealing sensitive information. Defending against viruses is possible by regularly carrying out predetermined measures as regularly as possible. Some essential steps that can be done to mitigate risks associated with viruses include installing antivirus software, which can be used to scan files and emails for viruses. These antivirus software should be regularly updated to detect the latest threats. Keeping software updated on a system is another important way to avoid being compromised. Viruses often exploit vulnerabilities in outdated software. Regularly update operating systems, applications, and plugins to patch known vulnerabilities. Be cautious with email attachments and avoid opening email attachments from unknown sources. Be especially vigilant if the email seems suspicious or unexpected.

Image Source: https://www.missioncriticalmagazine.com/articles/93186-biological-viruses-versus-computer-viruses
4. Trojan
Trojans, which is short for Trojan Horses, are malicious programs that disguise themselves as legitimate software in order to gain access to a system. Unlike viruses, Trojans do not self-replicate but instead create a backdoor for cybercriminals to access and control a compromised system. To defend against Trojans, there are precautionary measures to take that are different from if you were defending against viruses. Caution should be taken when downloading software and files from questionable sources. Be wary of free or cracked versions of paid software, as these are common carriers of Trojans. Use antivirus software to scan files and systems for Trojans. Some antivirus programs specifically target Trojans and other malware.
5. Denial of Service
Denial of Service (DoS) attacks are cyberattacks that disrupt the normal functioning of a computer system, network, or online service by overwhelming it with excessive volumes of traffic or requests. These attacks can render websites inaccessible, slow down network performance, and, in some cases, cause significant financial losses or damage to an organization’s reputation. There are many DOS attack techniques that can be used by an attacker when compromising a system. Some of them are:
- Ping Flood: Attackers can carry out flood attacks where they send out massive amounts of ICMP echo requests (ping) packets to a target to overwhelm its network.
- HTTP Flood: Attackers send massive amounts of HTTP requests to exhaust a web server’s resources and make it inaccessible to legitimate users.
- Botnets: Attackers control a network of compromised computers (botnets) to launch a coordinated DDoS attack, amplifying the attack’s strength.
- Slow Loris Attack: Attackers send partial HTTP requests, causing the target web server to keep connections open until resources are exhausted.
To defend against DoS attacks, a combination of proactive measures and responsive strategies is required:
- Intrusion Detection/Prevention Systems (IDS/IPS): Deploy IDS/IPS to monitor network traffic for suspicious patterns and automatically block or mitigate attacks.
- Traffic Analysis: Using network monitoring tools to detect abnormal traffic patterns and respond quickly.
- Traffic Filtering: Implement traffic filtering rules to prevent excessive requests or traffic from overwhelming your services.
- Regular Software Updates: Keep software and systems up to date to minimize vulnerabilities that attackers might exploit.
By implementing these measures and staying vigilant, organizations and individuals can reduce systems’ vulnerability to DoS attacks.
6. Exploitation
The pen-testing process involves exploitation to demonstrate the potential impact and severity of the identified vulnerabilities if they had been exploited by malicious actors. The exploitation phase carried out by ethical hackers involves attempting to exploit the identified vulnerabilities as a real attacker would. This may include trying to gain unauthorized access, escalate privileges, or execute malicious code. They may show how an attacker could exfiltrate and exploit sensitive data, disrupt services, or compromise critical systems. This report is shared with the organization’s security team. Reports allow companies to identify critical flaws in their security systems, give an assessment of their high-risk/high-impact vulnerabilities, and help train their security teams to stay one step ahead of evolving threats.
Conclusion
An attacker usually has multiple methods of trying to get into a user’s computer. The above examples are just one of many to demonstrate the smallest of changes and efforts can completely block access to a machine, slowing the attacker down. From updating software to changing passwords, the smallest things can make a huge difference.
Citation
Mission Critical Magazine. www.missioncriticalmagazine.com/articles/93186-biological-viruses-versus-computer-viruses.
Exploitation — Pentest-standard 1.1 Documentation. pentest-standard.readthedocs.io/en/latest/exploitation.html.
Handling Open Ports Secure and Finding Vulnerabilities. 16 Aug. 2022, blog.netwrix.com/2022/08/16/open-network-ports.
Richardson, Luke. “What Is Penetration Testing | Step-By-Step Process and Methods | Imperva.” Learning Center, 14 Mar. 2023, www.imperva.com/learn/application-security/penetration-testing.
Shekhar, Amar, and Amar Shekhar. “Top 10 Common Hacking Techniques You Should Know About.” Fossbytes, Oct. 2021, fossbytes.com/hacking-techniques.
