Tools for Defending Organizations with Advanced Threat Detection and Proactive Security Intelligence
September 20th, 2023
Authors: Ryan Morrissey and Annabel Otutu
Introduction

There are constantly changing threats and challenges that organizations and individuals face due to threats coming from the internet. Cyber-Security analysts commonly deploy a tool called Security Information and Event Management (SIEM) to improve upon strategies deployed in defending a network. This article serves to inform the reader about SIEM and has been curated to all levels of cybersecurity. When refering to SIEM tools, it is important to consider what they are and why they are so widely used in the cyber field. Let us explore some of the most widely recognized SIEM tools in cybersecurity today.
What is SIEM?
When talking about SIEM, there are two major components that help in understanding the concepts of the tool further. The two major components are SIM and SEM, which make up SIEM tools when combined.
Security Information Management (SIM) involves collecting security data from different endpoints that exist in a network. SIM primarily collects data from logs related to these endpoints by analyzing data as it comes through the network. When looking at raw log files for endpoints, it may be challenging to understand what’s going on so SIM tools collect important network data in a clean format such as system activities, IP addresses, MAC addresses, user info, and other data that could help with investigating.
Security Event Management (SEM) collects events that occur from devices on a network and oftentimes visualizes the events in different ways. Failed login attempts or high level access at odd times of the day/night or similar activities can be considered events. These two parts are very cohesive so it only makes sense to combine both of these components into one single tool; SIEM.
How SIEM Tools Work
There are tons of SIEM tools available for use, so it’s important to note that each tool varies in features, but for the most part each tool serves as a baseline for monitoring a network. Tracking security incidents across an organization’s network can be done with SIEM technology. They can continuously scan the network to make sure that an attacker has not gained access to the system. Frequent monitoring guarantees that in the event something was to happen, there would be a quick response to mitigate damage. SIEM tools first collect data from varying sources on your network. These tools can be very customizable so it’s important to configure the full scope of what you want monitored into the tool.
Often SIEM tools install ‘agents’ on every system that needs to be monitored. Logs are generated that can be correlated with the SIEM tool. Following the collection of data, SIEM tools are built to have detection systems in place as data is going through the network. SIEM tools are set up with certain algorithms that can detect out of the ordinary or even malicious activity on a network. The algorithms specifically have data sets of patterns or information sets such as malicious destination IPs, and when the algorithms detect those patterns or out of the ordinary incidents, it generates an alert that in some form is then sent to the security analyst. Ultimately, the customization and wide variety of tools to choose from is a large pro of SIEM tools because it allows the tool to adapt to each security team’s specific needs.
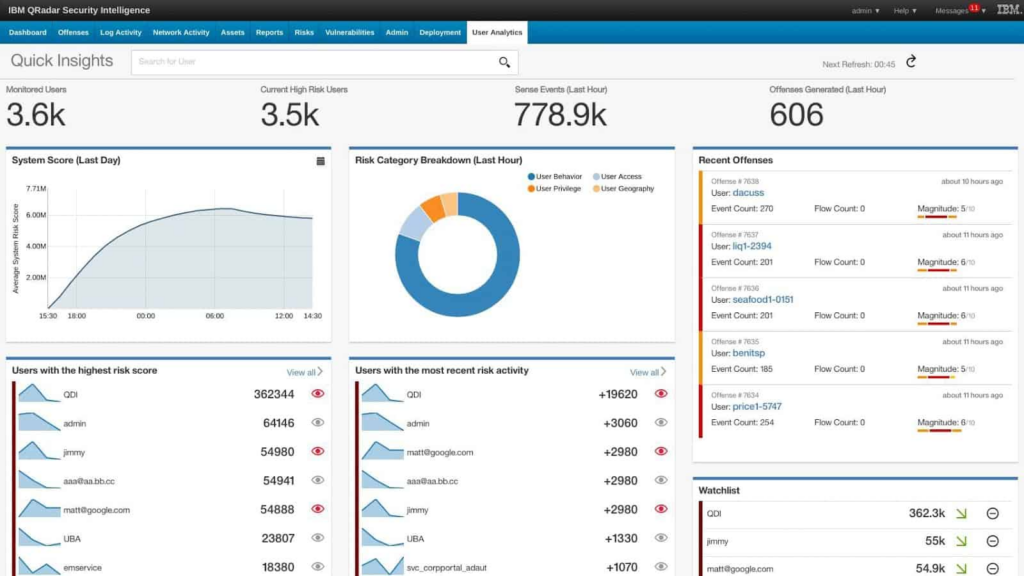
Image Source: (https://cdn.comparitech.com/wp-content/uploads/2018/04/SIEM8.jpg)
Common Features in SIEM
SIEM tools offer a wide range of features that allow you to manage any threats to your network for quick response if needed. It’s important when deciding which SIEM tool to deploy to look at what features that tool offers. Every tool has something specific that may meet your needs better. There are some features almost always seen in log management through one form or another include. For example, SIEM tools can grab logs from the different devices across your network and centralize them into the tool. Logs can be stored in case the need for analysis of these logs come up.
SIEM tools can also be customized with external threat feeds/data sets, which may be things like groups of malicious domains or IPs and this enhances detection among the logs going through the tool. There are often features in log management for sifting through logs. This process can be made easier by adding different filters and other search queries to narrow down any search when sorting through logs. Making sure your SIEM tools have chosen threat intelligence data added is important for getting the full potential of your tool.
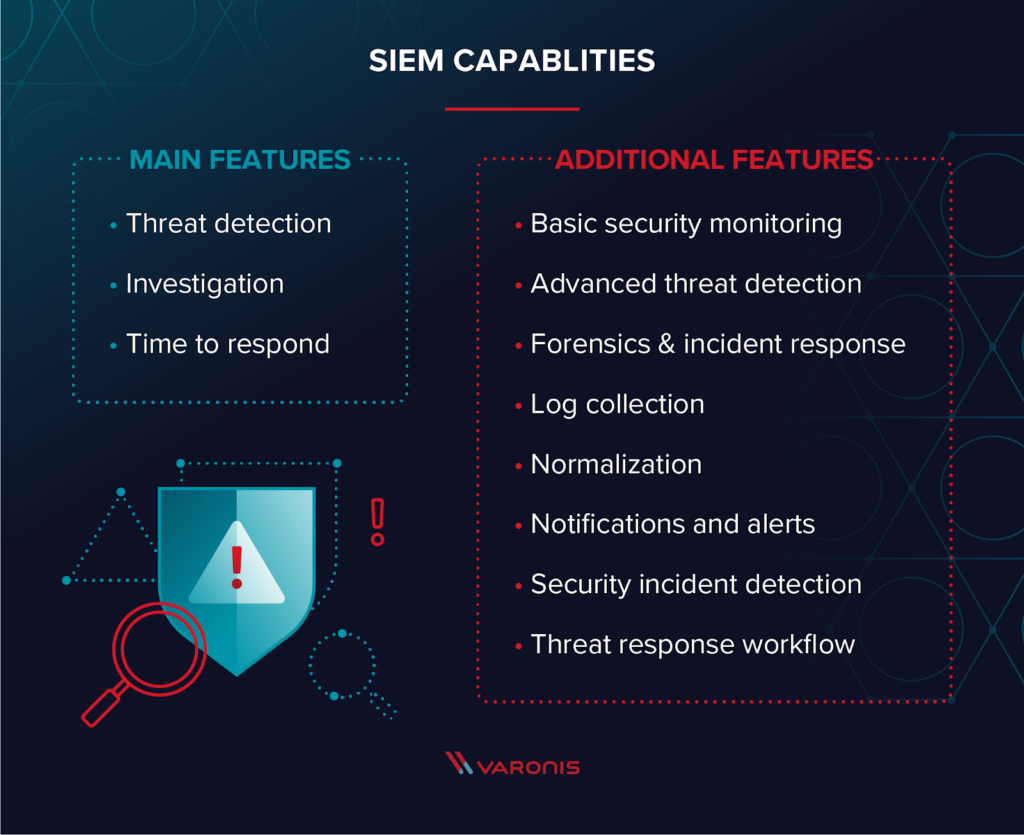
Image Source: (https://info.varonis.com/hubfs/Imported_Blog_Media/siem-capabilities-1.png?hsLang=en)
Alien Vault’s OTX (open threat exchange) is an example of a threat feed you might have added into your SIEM tool. OTX collects malicious IPS, Domains and URLs from a wide range of sources and will flag/ alert you if any source on your network connects to anything flagged in the OTX data set.
Oftentimes you will see data being visualized in various formats on SIEM tools. These visualizations usually appear on the main dashboard screen and give a quick look into what is happening currently in the network in a client-friendly format. These visualizations include different types of graphs such as bar or pie graphs and other tables of importance. SIEM tools also have in-depth monitoring of what users do on a network; tracking down what a user was doing before the malicious activity was alerted is essential to determine exactly what happened. SIEM tools are often set up to ensure that any suspicious activity detected triggers an alert. It’s impossible to check thousands if not millions of alerts generated on a network, so having alerts mark the logs that are suspicious makes tracking them down easier. SIEM tools are often at times just one part of a full security defense of a network; often times SIEM tools are setup to correlate with other security controls on your network. There are many other features that can be listed, but these are a good starting point for looking for what features you want in a SIEM tool. Having a SIEM tool setup with the proper features that tailors to what you need is definitely a much needed defense against maliciousness.
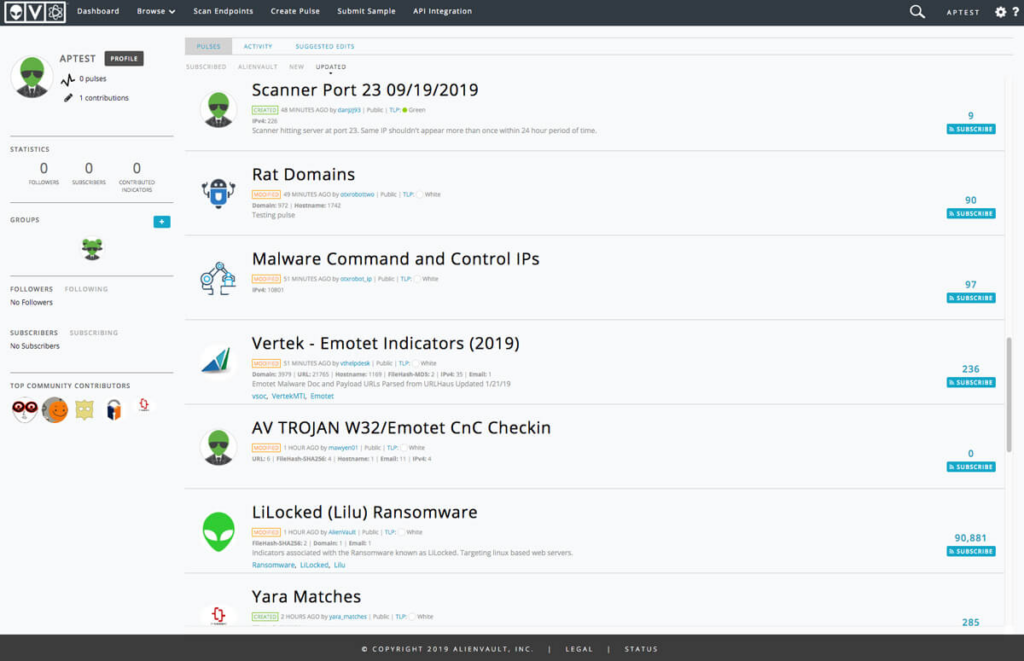
Image Source: (https://cdn-cybersecurity.att.com/images/uploads/product/tour/OTX_BrowsePulses.jpg)
What are the Benefits of SIEM?
Implementing a SIEM tool is a real asset to a security team. It brings a multitude of benefits when defending a network. SIEM tools main benefit is that it can centralize a different features other tools offer into one tool. SIEM can automate otherwise tedious tasks such as pointing out malicious logs for you and collecting logs for other investigations as well. Companies storing personal data often have to comply with certain standards showing that they are properly protecting data and SIEM can help check off multiple boxes to reach the proper compliance to be trusted with personal data. Overall SIEM offers a birds eye view over traffic flowing through your network and boosts your security team’s ability to respond to incidents as fast as possible. Context is everything when conducting investigations into threats like a police investigation, almost like SIEM serves as a proper partner for both finding and investigating these incidents by providing in depth data to further mitigate any risks for the future.
A major plus of SIEM is that it’s almost always a true value for money for a business when implementing. Depending on the setup of your network, you may need the services of a paid SIEM, but there are free options too. The early detection of threats allows for the mitigation of a lot of attacks, which in the end saves tons of money. Minimizing cyber threats automatically minimizes financial loss. The overall efficiency with the abundance of features allows you to save from having to purchase other applications. SIEM tools main goal is to centralize most security controls into a single tool. The automation allows technicians to focus on other issues and alerts that come through to them; time is money. The prevention of data loss is the main goal of security and SIEM tools are a good start to protecting data in a network. Saving data for a company is often saving money and incoming customers. Nobody wants to be known as the company that was hacked because they didn’t have proper security in place.
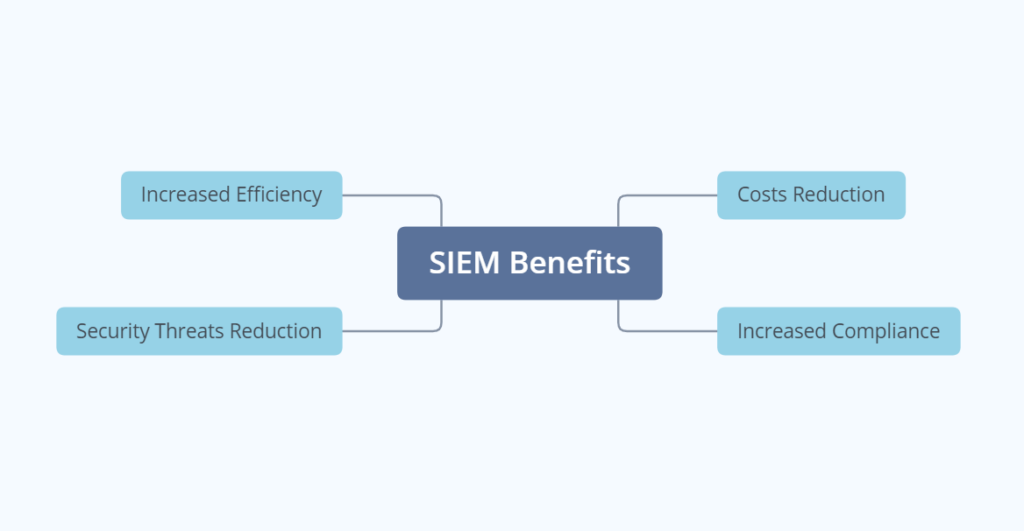
Image Source: (https://heimdalsecurity.com/blog/wp-content/uploads/what-is-siem-benefits.png)
Considerations and Challenges when Implementing a SIEM
Before you decide which SIEM you want, it’s important to take some factors into account that could influence your decisions. Some of the overall scope things you should layout would be again, the specific needs of security of your network, how your network is built and lastly, what is the budget for the deployment. A SIEM takes manpower as well, and although a lot of it can be automated, it still requires active monitoring and someone ready to respond to any malicious traffic detected. Having the proper training and skills necessary would be a major factor if you decide to deploy a SIEM tool. Newly deployed tools like SIEM tools, where you’re talking tons of features and millions of logs, it can take time to tune the tool exactly how you want after you deploy it. It’s just important to keep in mind that the deployment won’t be perfect and you will have to be prepared to take out things like false alarms and make other changes to your tool to make it up to the standards that will provide proper defense. To stay effective, SIEM tools have to be constantly updated and up to date with what it is looking for. When handling sensitive data of any type, especially with a powerful tool like SIEM, you have to follow the proper ethics and comply with regulations that come with collecting data.
SPLUNK
Splunk is one of the most widely used SIEM tools in the Cyber world. It serves as an extensive index of massive amounts of data from various sources on devices on your network. Splunk processes every piece of data in real time and even allows you to extensively search through it all with its own search query language.
Splunk is also thought to be one of the most user friendly SIEM tools while being one of the most data driven/complex on the backend. It’s highly customizable so you can make it look like what you want it to look like. Highly customizable widgets and tables of data to show what’s going on based completely off what you prefer. If you want to add something on the dashboard, to create it, drag it onto your screen, vice versa if you don’t need something on your dashboard. Splunk has a easy to digest log observer feature shown below (might have to enlarge). You can query searches and use different fields to organize how the data is output to you, the log tool collects every log so future analysis can be conducted if needed and converts complex data into an organized format.
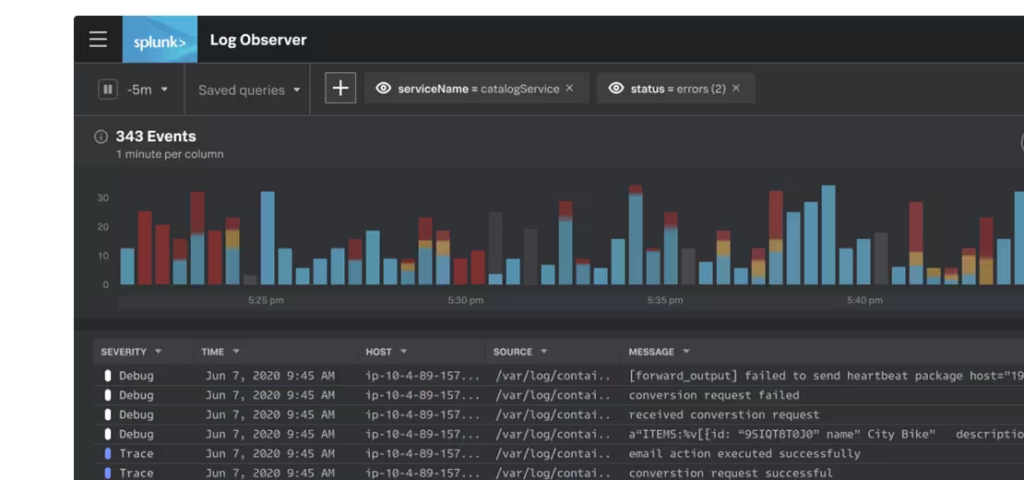
Image Source: (https://www.splunk.com/en_us/products/observability.htmI)
Splunk Search Processing Language (SPL) can be a powerful feature that narrows down searches and is an overall highlight that separates Splunk from the rest of the tools making it more flexible. When there’s millions of connections and events happening on the network, using the proper filters, with what information will help track down what you need. There are various commands, operators and even functions like other coding languages but are used specifically for search queries. The ability to sift through large amounts of data with these highly customizable searches is a highly suitable way to run investigations. Cheat sheet provided below to help learn the basics of SPL.
Image Source: https://i.imgur.com/py44vwB.png
There are also rich amounts of resources available provided both by Splunk and by other sources that can be found on the internet, anything from documentation for a full setup or training on how to actually use the product. A link can be found below for some Splunk installations and resources for getting started. There are factors to consider when installing splunk, it’s flexible in the fact you can install it on premise to a device you own or it can be run from the cloud. There are free options but those do not come with all the features. The pricing for Splunk scales the more devices you need to have covered. Splunks dedicated community is massive as well, with people always ready to answer any questions that may come up. There are specific forums on splunks website (link below) that provide all sorts of insight into a massively powerful product.
Splunk links
- SPL cheat sheet: https://docs.splunk.com/images/a/a3/Splunk_4.x_cheatsheet.pdf
- Splunk Forums: https://community.splunk.com/t5/Community/ct-p/en-us
- Splunk Downloads: https://www.splunk.com/en_us/download.html
- Splunk Free: https://docs.splunk.com/Documentation/Splunk/9.1.0/Admin/MoreaboutSplunkFree
Source: https://www.splunk.com/content/dam/splunk-blogs/images/en_us/2023/02/splunk-ui-dashboard-2.png
IBM QRadar
QRadar is another example of an SIEM tool that is widely used in organizations today. Qradar was developed and is maintained by IBM, it contains several advanced features that enhance security. IBMs name holds well among the IT space and also makes this product more easily approvable to deploy due to its recognizable name. Qradar specializes in being pre-equipped with popular threat feeds and is easily customizable to add more, this allows detection of real time threats. It also allows for easy integration with third party features that can enhance QRadar. A major advantage and highlight of Qradar is how advanced its threat detection algorithm is. Using millions of previous events and analytics including network behavior, user behavior it detects out of the ordinary behavior, so it can be flagged for review. Every movement is tracked by Qradar and if the movement matches a tactic of an attack (MITRE attack tactics auto detected by Qradar) it will calculate the risk of the behavior and also have the security technician explore that behavior further.
Qradar is easily installed either through hardware or software. Splunks pricing is based on total data usage while QRadar measures its rate by how many alerts per second are being generated on the network. While Qradar can be integrated with any device generating network traffic, it works even better with IBM products. The search filters are also highly customizable and extensive. For log search inquiries, there is the option of creating filters with custom parameters or using already existing filters. Overall Qradar is easy to deploy and has great log reporting features to give you the most data possible. Its a tool that uses its wide range of resources to detect anything that may serve as malicious for your network. Qradar is a flexible/ scalable option backed by IBM and is growing as one of the strongest SIEM products on the market.
Citations
“Advanced Threat Detection – Security Qradar Siem.” IBM, www.ibm.com/products/qradar-siem/advanced-threat-detection. Accessed 7 Aug. 2023.
Cooper, Stephen. “5 Best Threat Intelligence Feeds.” Comparitech, 1 June 2023, www.comparitech.com/net-admin/best-threat-intelligence-feeds/.
“Crowd-Sourced Threat Intelligence: Alienvault Open Threat ExchangeTM (OTX).” The Hacker News, 14 July 2014, thehackernews.com/2014/07/crowd-sourced-threat-intelligence.html.
IBM Qradar® Security Information and Event … – Tech Business News, www.techbusinessnews.com.au/blog/ibm-qradar-security-information-and-event-managementsiem/. Accessed 7 Aug. 2023.
Ibm. “IBM Launches New QRadar Security Suite to Speed Threat Detection and Response.” PR Newswire: Press Release Distribution, Targeting, Monitoring and Marketing, 24 Apr. 2023, www.prnewswire.com/news-releases/ibm-launches-new-qradar-security-suite-to-speed-threat-detection-and-response-301804789.html.
Nichols, Crystal. “5 Siem Challenges That Cause the Most Stress.” Cybriant, 13 July 2023, cybriant.com/siem-challenges/.
“Observability Products & Solutions.” Splunk, www.splunk.com/en_us/products/observability.html. Accessed 7 Aug. 2023.
“QRadar vs Splunk: Top 13 Differences You Should Know.” EDUCBA, 7 July 2023, www.educba.com/qradar-vs-splunk/#:~:text=Specialization%3A%20QRadar%20specializes%20mostly%20in,and%20handle%20security%2Drelated%20subjects.
Scarfone, Karen. “What Siem Features Are Essential for Your Company?: TechTarget.” Security, 28 Sept. 2017, www.techtarget.com/searchsecurity/feature/How-to-find-the-best-SIEM-system-for-your-company.
“Splunk Log Analysis with Log Observer: 5 Key Capabilities.” Exabeam, 23 Mar. 2023, www.exabeam.com/explainers/log-management/splunk-log-analysis-with-log-observer-5-key-capabilities/#:~:text=With%20Splunk%20Log%20Observer%2C%20you,and%20performance%20of%20your%20systems.
“Splunk: What It Is, Why Companies Need It.” ICT Services, Supply Chain, Emergency Management – Scopri Di Più Sul Blog Di Beta 80, news.beta80group.it/en/splunk-what-it-is-why-companies-need-it#:~:text=The%20great%20benefit%20of%20Splunk,current%20and%20constantly%20evolving%20scenario. Accessed 7 Aug. 2023.
Stoltzfus, Justin. “What’s the Difference between Sem, Sim and Siem?” Techopedia, 31 Mar. 2022, www.techopedia.com/7/31201/security/whats-the-difference-between-sem-sim-and-siem.
“What Is Siem?” Microsoft Security, www.microsoft.com/en-us/security/business/security-101/what-is-siem. Accessed 7 Aug. 2023.
