Criminal targeting spyware gone wrong
May 18th, 2023
Author: Lily Pouliot
What is Pegasus?
Pegasus is spyware that was created in 2016. It can be installed on mobile phones or devices running iOS or Android. It was originally sold as a “serious crime and terrorism” surveillance tool. The app itself is zero-click exploit software. Someone can discreetly download spyware on the iPhone by opening an iMessage, and the user may not know it was installed. In a recent 2022 update, Pegasus was able to access a target’s microphone and camera and harvest information from other apps.

Spyware can also read text messages, view call logs, collect passwords, and track locations. The name Pegasus comes from Greek mythology, as it is a winged horse. Spyware is also a Trojan horse, also from Greek mythology.
After a failed installation attempt on a human rights activist’s iPhone in August 2016, Pegasus was discovered. An investigation was conducted, revealing details about spyware’s abilities and security vulnerabilities. Pegasus was the first malicious remote exploit to use jailbreaking, the process of changing permissions to remove software restrictions, to gain restricted access to an iPhone. Soon afterward, there was an investigation conducted in July 2021 called the Pegasus Project. A thorough analysis by the human rights organization Amnesty International followed. From the Guardian, Pegasus has targeted “38 journalists in Morocco, 48 journalists in Azerbaijan, 12 journalists in the United Arab Emirates, and 38 journalists in India.” It was reported that Pegasus is still surveilling political leaders, anti-regime activists, heads of state, and around 200 journalists from 24 countries.

Image Source: https://www.cryptomuseum.com/covert/sw/nso/pegasus/
Origins of Pegasus
Pegasus production and distribution originate from an Israel-based company, NSO (Niv, Shalev, and Omri). Shalev Hulio co-founded the private company in 2010. It was sold as criminal surveillance and wasn’t supposed to target activists, journalists, or politicians. However, there have been reports and lawsuits about other hacks that have had an impact on the business, one of which was a reported hack in 2018 against Amazon founder Jeff Bezos. There was also a lawsuit in 2018 from a Saudi objector when it hacked a device belonging to journalist Jamal Khashoggi. He was murdered inside the Saudi embassy the same year. All of these hacks can be traced back to the Pegasus software NSO released. The company claims the software is a valuable product as it comes back against encrypted tech criminals and terrorists.
The New Yorker found details about some of the NSO group’s inner workings. It found that Pegasus was similar to military equipment that countries regularly sell to other countries. It also found some interesting, detailed Google analysis of one of the Pegasus attack mechanisms appearing on NSO’s wall.
NSO has gotten itself into a few lawsuits over the past few years due to the Pegasus app. Whatsapp, the instant messaging app, started a lawsuit claiming NSO created an exploit through the Whatsapp calling feature. This exploit allowed spyware, not Pegasus, to enter the app. “1,400 users were victims of this exploit, with around 100 of them being human rights activists, journalists, and other perceived threats to a government” (Nord). Despite all of the evidence pointing to the spyware attack, NSO denied targeting the victims. However, they did not deny the breach. The second lawsuit took place in 2021 and revolved around Apple and Pegasus spyware. It was another security exploit that allowed the spyware app to enter Apple’s devices. They seek to ban the group’s software on Apple devices and make NSO locate and delete any private data on its app, along with disclosing the profits made from these operations.

Image Source: https://www.nsogroup.com/
Pegasus Attacks
For the first wave of attacks recorded in 2016, Pegasus infected phones through phishing. The victim would receive text messages embedded with malware. If the link in the notification is clicked on, the phone is instantly infected with the Pegasus virus. According to a former NSO employee, the Pegasus found in the U.S. had one-click capabilities for all phones except for old Blackberry phones, which could be corrupted with a zero-click attack. It wasn’t until 2019 that WhatsApp, a messaging app that sends messages over a network instead of a phone network, spotted an issue regarding Pegasus. Zero-click attacks were completed through the app by calling the target’s phone number. Even if the call wasn’t answered, spyware could still install itself. The Pegasus malware also relies on iPhone iMessage vulnerabilities, just as the spyware now relies on iPhone iMessage to infect phones. The last major shift occurred in 2020, when Pegasus moved to zero-click exploits and network attacks. These methods allowed spyware to break into phones without user interaction or leaving detectable traces.
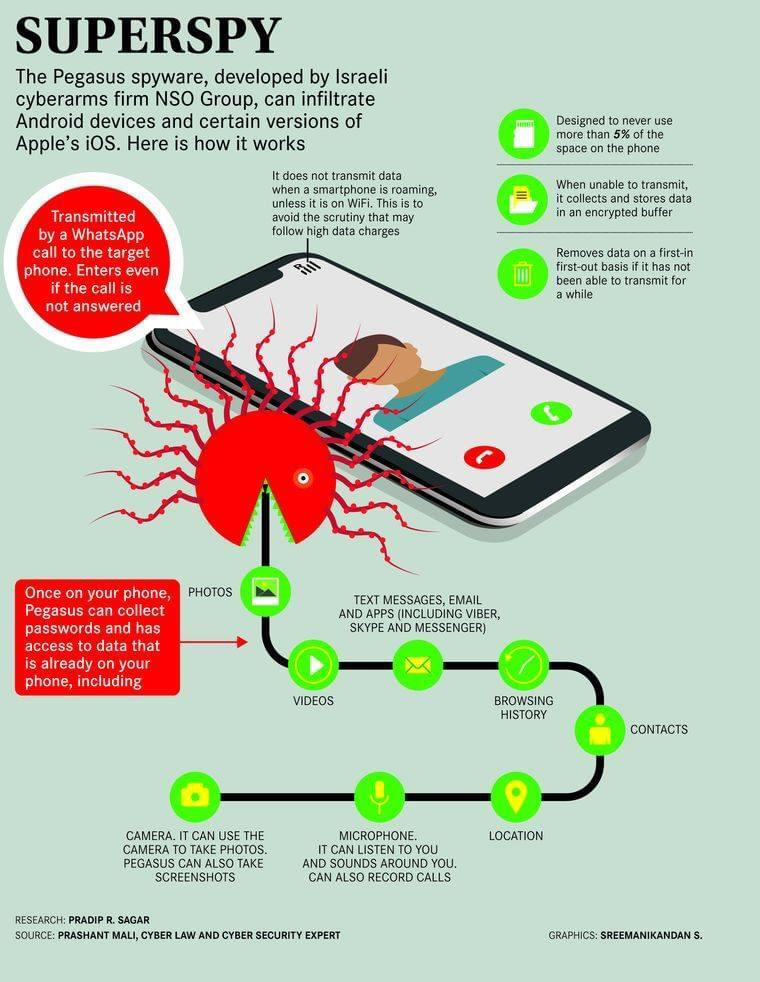
Image Source: https://blog.avast.com/pegasus-and-spyware-avast
An investigation into Pegasus by Amnesty International led to a breakthrough in 2021. It was revealed that the spyware employed a command-and-control (C&C) infrastructure, a “set of organizational and technical attributes and processes… [that] employ human, physical, and information resources to solve problems and accomplish missions”. That type of infrastructure was used to deliver exploited payloads and send commands to Pegasus targets. There are also a few known iterations of this C&C infrastructure, called the Pegasus Anonymized Transmission Network (PATN) by the NSO. Each group has about 500 domain names, multiple DNS servers, and other network infrastructure for itself. To avoid internet scanning on their online infrastructures, PATN registers several high port numbers. To also avoid getting caught, PATN also uses up to three randomized subdomains and URL paths per exploit attempt.
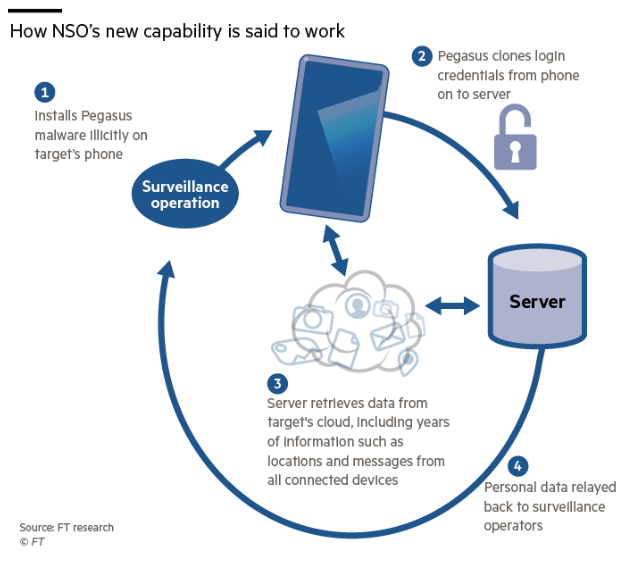
Image Source: https://www.cloudmanagementinsider.com/pegasus-spyware-new-security-threat-to-tech-giants-cloud/
Reactions and Consequences
A nonprofit organization named Forbidden Stories in Paris and a human rights group called Amnesty International shared a list with 17 news organizations. This list held more than 50,000 phone numbers of people suspected of being NSO customers. Other news sites confirmed the numbers and identities on the list and the infections on their phones. Of the 67 phones on the list, 37 showed signs of Pegasus installation or attempted installation. Out of those 37 phones, 34 were Apple iPhones. Most of these attacks target Apple’s phones, which hurts the company’s reputation when it comes to tech security. However, the company has stated it will donate 10 million U.S. dollars to any damages from organizations advocating for privacy and conducting research on online surveillance. Even though Apple reported making 20.5 billion U.S. dollars that same year, the money still helped smaller organizations.
Another organization named Citizen Lab revealed that Pegasus infected at least 51 people in Spain, specifically in the Catalonia region. For some background information, Catalonia is seeking political independence from Spain, but Spanish police have taken down the independence movement. The Chief Executive of NSO, Shalev Hulio, reported that Spain had procedures to ensure the use was legal, but Citizen Lab said Pegasus attacks targeted Jordi Solé, a pro-independence member of the European Parliament. The spyware also targeted digital security researcher Elies Campo and Campo’s parents.
The NSO Group was cut off as a US product customer. It was a very significant move, as the NSO needed the U.S. company’s computer processors, phones, and developer tools. This was “to maliciously target government officials, journalists, businesspeople, activists, academics, and embassy workers. These tools have also enabled foreign governments to conduct transnational repression,” stated the U.S. Commerce Department. French President Emmanuel Macron changed his mobile number and requested heightened security measures after the list of 50,000 numbers found in the NSO database was leaked. The President also held a national security conference to raise concerns about Pegasus with Israeli Prime Minister Naftali Bennett. Israel created a commission to look into the Pegasus problem. On July 28, Israeli defense authorities inspected NSO offices in person.
Works Cited:
- Evangelist, Cloud. “Pegasus Spyware: A New Threat to Tech Giants’ so Called ‘Secure’ Cloud.” Cloud Management Insider, 29 Nov. 2019, https://www.cloudmanagementinsider.com/pegasus-spyware-new-security-threat-to-tech-giants-cloud/. Author name is a pseudonym.
- Farrier, Ellie. What Is Pegasus Spyware and Is Your Phone Infected with Pegasus?, 30 Sept. 2022, https://www.avast.com/c-pegasus-spyware#:~:text=Pegasus%20spyware%20is%20zero%2Dclick,a%20device%27s%20microphone%20and%20camera.
- Haskell-Dowland , Paul, and Roberto Musotto. “How Does the Pegasus Spyware Work, and Is My Phone at Risk?” The Conversation, The Conversation US, Inc., 20 July 2021, https://theconversation.com/how-does-the-pegasus-spyware-work-and-is-my-phone-at-risk-164781.
- Shankland, Stephen. “Pegasus Spyware and Citizen Surveillance: Here’s What You Should Know.” CNET, 19 July 2022, https://www.cnet.com/tech/mobile/pegasus-spyware-and-citizen-surveillance-what-you-need-to-know/.
- Unlisted. “Command and Control.” Wikipedia, Wikimedia Foundation, 6 Apr. 2023, https://en.wikipedia.org/wiki/Command_and_control.
- Unlisted. “NSO Group.” Wikipedia, Wikimedia Foundation, 1 Apr. 2023, https://en.wikipedia.org/wiki/NSO_Group.
- Unlisted. “Pegasus (Spyware).” Wikipedia, Wikimedia Foundation, 28 Mar. 2023, https://en.wikipedia.org/wiki/Pegasus_(spyware)#Background.
- Unlisted. “Pegasus Project (Investigation).” Wikipedia, Wikimedia Foundation, 5 Mar. 2023, https://en.wikipedia.org/wiki/Pegasus_Project_(investigation).
- Unlisted. “Pegasus.” Crypto Museum, https://www.cryptomuseum.com/covert/sw/nso/pegasus/.
- Whitmore, Charles. “Pegasus Spyware: What Should You Know?” NordVPN, 9 May 2022, https://nordvpn.com/blog/pegasus-spyware/.
